Jadi begini kurang lebih gambarannya:
To The Point:
- Login to AWS Console
- Goto VPC > VPN Connection > Customer Gateways
- Create Customer Gateway
Name: name of Customer Gateway
Routing: Static
IP Address: Your Office
Public IP Address
- Goto VPC > VPN Connection > Virtual Private Gateways
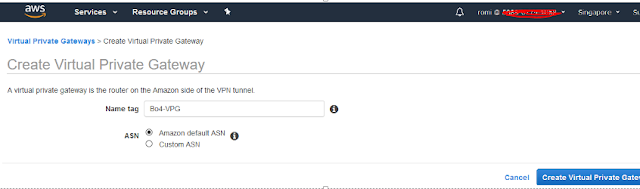
- Create Virtual Private Gateway
Name: Name Of your VPG
ASN: Amazone by Default
- Then Attach VPC to your Virtual Private Gateways
- Goto VPC > VPN Connection > VPN Connections
Name tag: Your VPN Name
Virtual Private Gateway:
Select your VPG
Customer Gateway ID: Selec
your CG id
Routing Option: Your Local IP
(Green / local LAN IPFire) and CIDR
- Download Configuration > Generic > Download
- Enable Route Propagation
Goto VPC > Route Tables > Select Subnet > Route Propagation
> Edit > [Propagate YES]
10. Open Configuration File from AWS
GO TO IP FIRE
- Go to Services > IPSec
- Scroll to Connection Status and Control > add
- Select Net-To-Net Virtual Private Network > add
Name: Name of your IP Sec
Enabled: [yes]
Remote host/IP: IP from AWS VPN Configuration File (Virtual Private
Gateway / Outside IP Address)
Local Subnet: GREEN IP / Local IP Ipfire
Remote subnet: IP address from AWS VPC / AWS Subnet (Local EC2 IP)
Edit advanced Setting: [tick yes]
Use pre-shared key: Paste from AWS VPN Configuration File
Save
- Advanced Configuration
Keyexchange: IKEv1
Encription
: 128 bit AES CBC
|
128 bit
AES CBC
|
Integrity:
SHA1
|
SHA1
|
Lifetime:
8 H
|
1 H
|
Grouptype:
just leave default
|
just leave default
|
- Save
- Make sure connection is Connect!
- Go to Firewal > Firewall Rules > add
Source: Standard networks GREEN
NAT: Source NAT (GREEN)
Destination: IPSec Network : your ipsec Name
Save
DNS FORWARDING
- Go to Network > DNS Forwarding
- Zone: Name off DNS Forwaring
- Nameserver : your AWS VPC Subnet / IP Address (Local EC2 IP)
- Enabled: Tick [yes]
- Add
- (If Needed, add DNS Forwarding again if you have more VPC Subnet)
TESTING
Now Ping
your local EC2 IP Address
DONE!